APPLIES TO:  Azure Database for PostgreSQL - Flexible Server
Azure Database for PostgreSQL - Flexible Server
This article provides step-by-step instructions to enable or disable a system assigned managed identity for an Azure Database for PostgreSQL flexible server.
Steps to enable for existing servers
Using the Azure portal:
Locate your server in the portal, if you don't have it open. One way to do it is by typing the name of the server in the search bar. When the resource with the matching name is shown, select that resource.

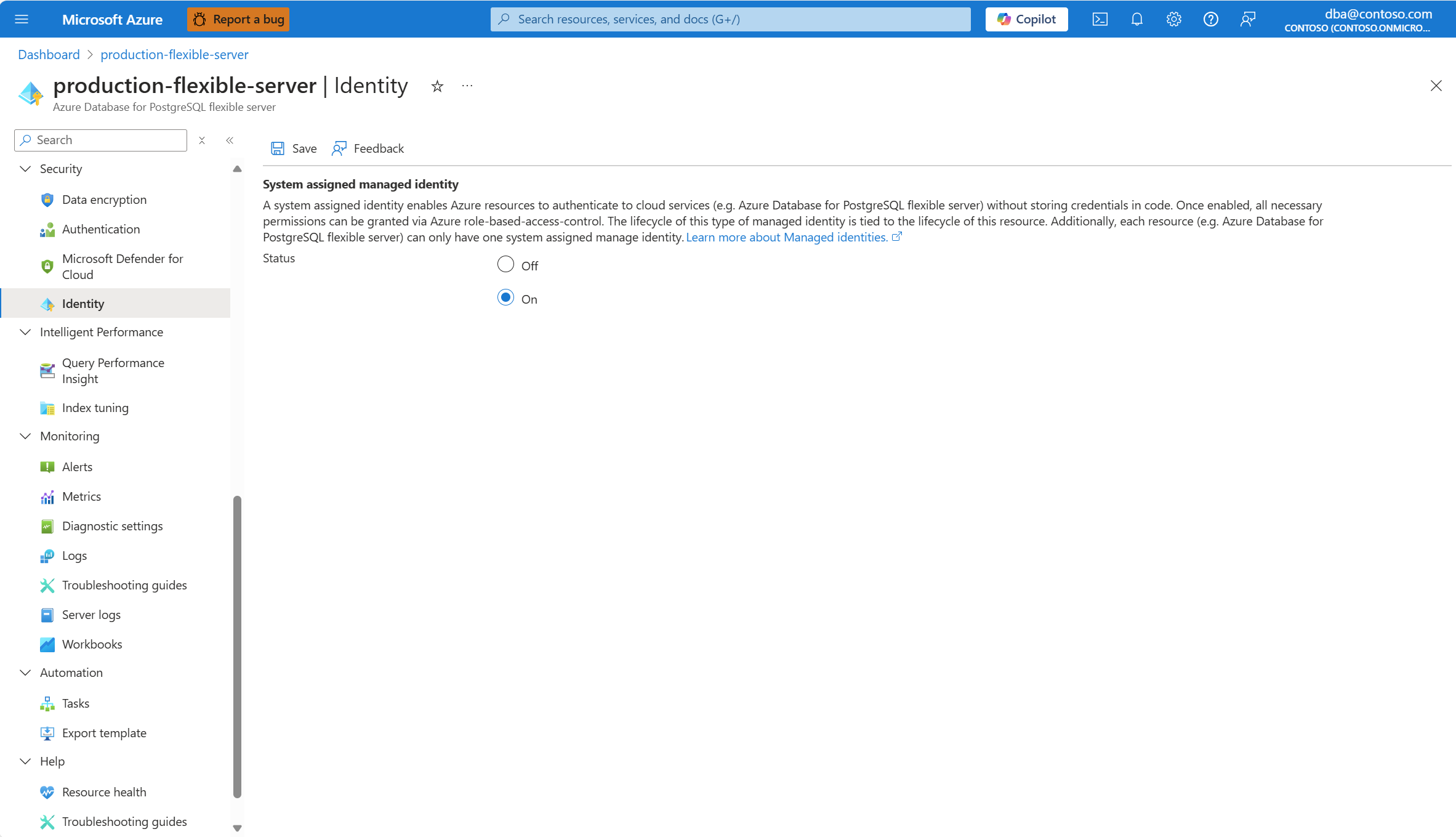
In the resource menu, under Security, select Identity.

In the System assigned managed identity section, select On.

Select Save.
If the server has data encryption configured to use customer managed keys, it isn't supported to disable the system assigned managed identity of the server once you enable it. For that reason, if that condition is detected, you're requested to confirm that you want to enable the system assigned managed identity.

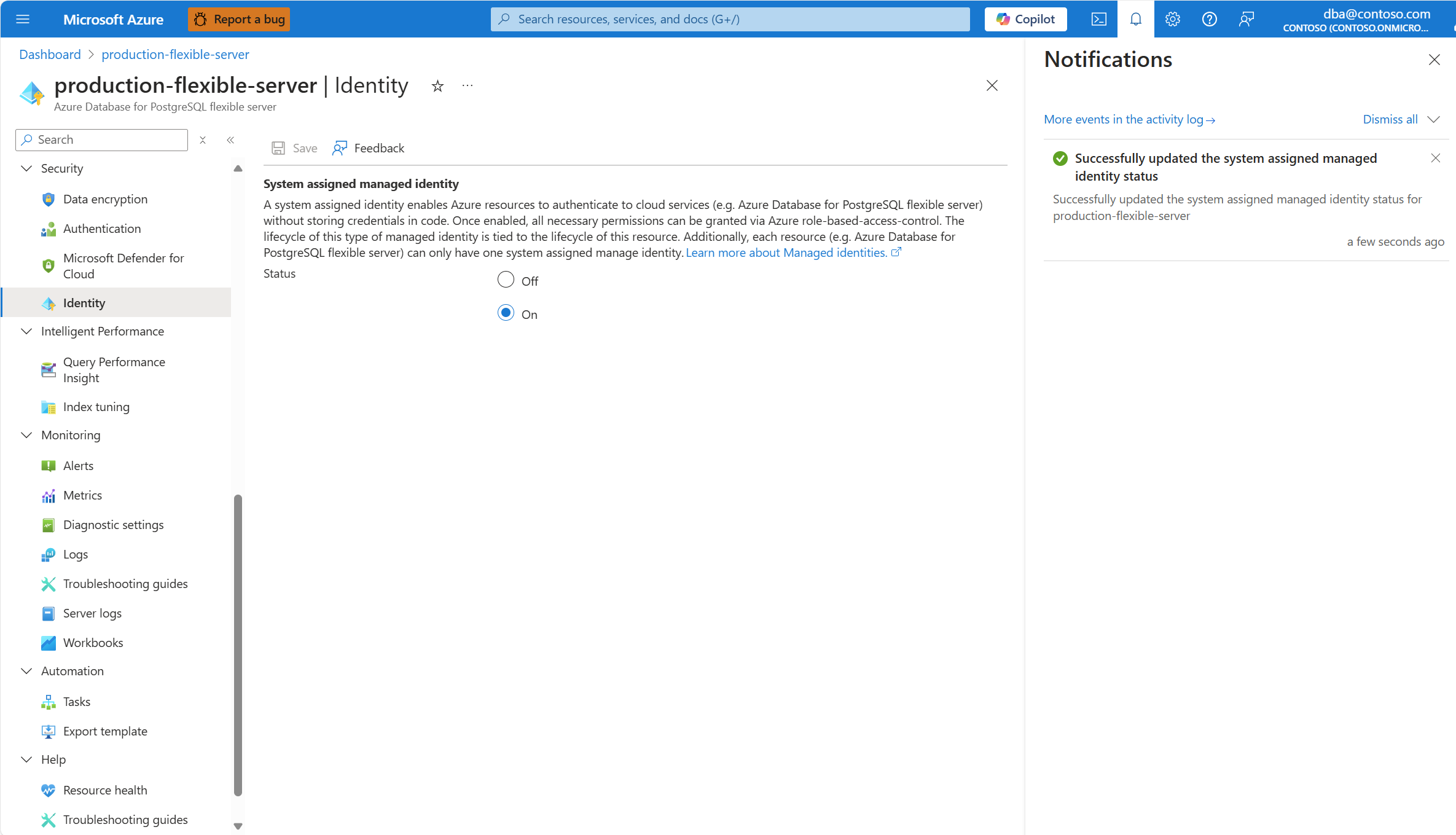
When the process completes, a notification informs you that the system assigned managed identity is enabled.
The az postgres flexible-server update command doesn't provide built-in support to enable and disable the system assigned managed identity yet. As a workaround, you can use the az rest command to directly invoke the Servers - Update REST API.
# Enable system assigned managed identity
subscriptionId=<subscription-id>
resourceGroup=<resource-group>
server=<server>
result=$(az postgres flexible-server show --resource-group $resourceGroup --name $server --query "identity.type" --output tsv)
if [ -z "$result" ]; then
az rest --method patch --url https://management.azure.com/subscriptions/$subscriptionId/resourceGroups/$resourceGroup/providers/Microsoft.DBforPostgreSQL/flexibleServers/$server?api-version=2024-08-01 --body '{"identity":{"type":"SystemAssigned"}}'
elif [ "$result" == "UserAssigned" ]; then
az rest --method patch --url https://management.azure.com/subscriptions/$subscriptionId/resourceGroups/$resourceGroup/providers/Microsoft.DBforPostgreSQL/flexibleServers/$server?api-version=2024-08-01 --body '{"identity":{"type":"SystemAssigned,UserAssigned"}}'
else
echo "System Assigned Managed identity is already enabled."
fi
Steps to disable for existing servers
Using the Azure portal:
Locate your server in the portal, if you don't have it open. One way to do it is by typing the name of the server in the search bar. When the resource with the matching name is shown, select that resource.

In the resource menu, under Security, select Identity.

In the System assigned managed identity section, select Off.

Select Save.

When the process completes, a notification informs you that the system assigned managed identity is disabled.

The az postgres flexible-server update command doesn't provide built-in support to enable and disable the system assigned managed identity yet. As a workaround, you can use the az rest command to directly invoke the Servers - Update REST API.
# Disable system assigned managed identity
subscriptionId=<subscription-id>
resourceGroup=<resource-group>
server=<server>
result=$(az postgres flexible-server show --resource-group $resourceGroup --name $server --query "identity.type" --output tsv)
if [ "$result" == "SystemAssigned" ]; then
az rest --method patch --url https://management.azure.com/subscriptions/$subscriptionId/resourceGroups/$resourceGroup/providers/Microsoft.DBforPostgreSQL/flexibleServers/$server?api-version=2024-08-01 --body '{"identity":{"type":"None"}}'
elif [ "$result" == "SystemAssigned,UserAssigned" ]; then
echo "System Assigned Managed identity cannot be disabled as the instance has User Assigned Managed identities assigned."
else
echo "System Assigned Managed identity is already disabled."
fi
Steps to show currently assigned
Using the Azure portal:
Locate your server in the portal, if you don't have it open. One way to do it is by typing the name of the server in the search bar. When the resource with the matching name is shown, select that resource.

In the resource menu, select Overview

Select JSON View.
In the Resource JSON panel that opens, find the identity property and, inside it, you can find the principalId and tenantId for the system assigned managed identity.

# Show the system assigned managed identity
resourceGroup=<resource-group>
server=<server>
az postgres flexible-server identity list \
--resource-group $resourceGroup \
--server-name $server \
--query "{principalId:principalId, tenantId:tenantId}" \
--output table
Steps to verify in Microsoft Entra ID
Using the Azure portal:
Locate the Enterprise Applications service in the portal, if you don't have it open. One way to do it is by typing its name in the search bar. When the service with the matching name is shown, select it.

Choose Application Type == Managed Identity.
Provide the name of your instance of Azure Database for PostgreSQL flexible server in the Search by application name or object ID text box.

# Verify the system assigned managed identity
server=<server>
az ad sp list --display-name $server
Related content
 Azure Database for PostgreSQL - Flexible Server
Azure Database for PostgreSQL - Flexible Server













